About
The Mobb MCP Server enables AI assistants to scan local Git repositories, detect security vulnerabilities using SAST data, and generate automated code fixes for developers to review and commit.
Capabilities
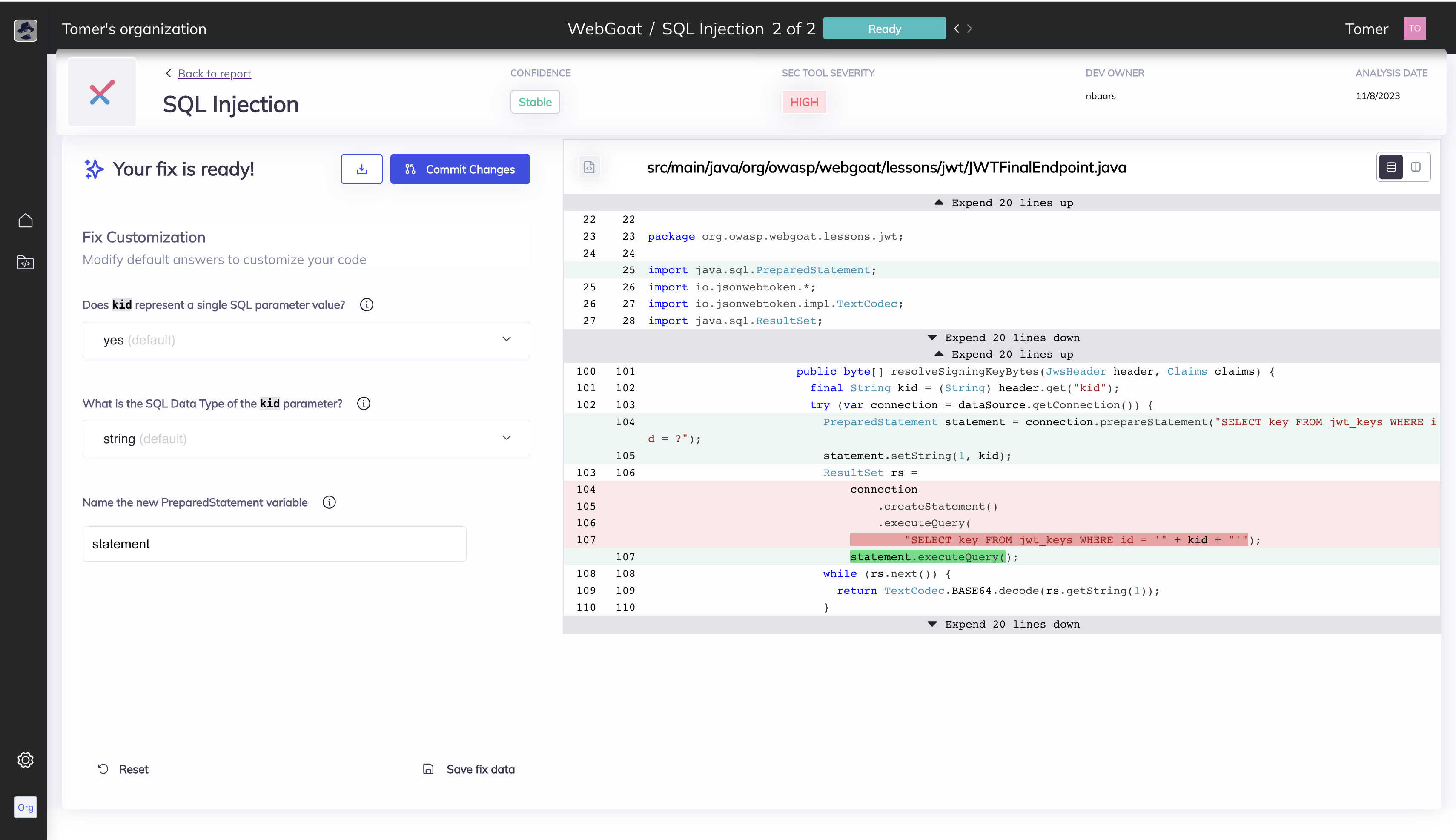
Bugsy is a lightweight command‑line interface that brings automated security remediation to any codebase. It bridges the gap between static application security testing (SAST) tools and developers by automatically converting identified vulnerabilities into concrete code patches. By doing so, it turns the tedious process of manual fix generation into a single, repeatable command that can be integrated into continuous integration pipelines or run locally by developers.
The tool operates in two complementary modes. In Scan mode, Bugsy invokes supported SAST engines such as Checkmarx or Snyk directly against a public GitHub, GitLab, or Azure DevOps repository. It then parses the generated report, filters for issues that can be remediated automatically, and produces a set of pull‑request‑ready patches. In Analyze mode, users supply an existing vulnerability report from Checkmarx, CodeQL, Fortify, or Snyk; Bugsy processes the file in the same way, generating fixes that can be reviewed and merged. This duality allows teams to choose between an end‑to‑end automated workflow or a more controlled, report‑driven approach.
For developers working with AI assistants, Bugsy’s MCP server capability is a game‑changer. By exposing its scan and analyze functions as Model Context Protocol endpoints, Claude or other assistants can trigger vulnerability scans on the fly, receive a list of suggested patches, and even propose pull requests—all within the assistant’s conversational interface. This tight integration removes friction between security tooling and developer workflows, enabling instant remediation suggestions without leaving the chat environment.
Key features that make Bugsy valuable include:
- Vendor‑agnostic: Supports multiple SAST tools, so teams can keep their existing security stack while adding automated fixes.
- Automatic patch generation: Converts findings into actionable code changes, dramatically reducing the time from detection to resolution.
- MCP compatibility: Exposes its functionality as a server that AI assistants can call, opening up new possibilities for intelligent code review and continuous improvement.
- CLI simplicity: One‑line commands ( or ) make it easy to drop into any workflow, from local development to CI pipelines.
Real‑world scenarios where Bugsy shines include continuous integration environments that need rapid feedback on new commits, security teams that want to surface fixes without manual triage, and AI‑augmented development workflows where an assistant can suggest patches in real time. By automating the most repetitive part of vulnerability remediation, Bugsy frees developers to focus on higher‑level design and business logic, while ensuring that security gaps are addressed before they reach production.
Related Servers
n8n
Self‑hosted, code‑first workflow automation platform
FastMCP
TypeScript framework for rapid MCP server development
Activepieces
Open-source AI automation platform for building and deploying extensible workflows
MaxKB
Enterprise‑grade AI agent platform with RAG and workflow orchestration.
Filestash
Web‑based file manager for any storage backend
MCP for Beginners
Learn Model Context Protocol with hands‑on examples
Weekly Views
Server Health
Information
Explore More Servers
Endor MCP Server
Instant sandboxed services for AI agents and developers
MCP Dust Server
Seamless MCP integration with Dust AI agents for real‑time streaming
Tusky MCP Server
Bridge Tusky storage to AI assistants via MCP
Quiz MCP Server
AI‑powered quiz generator for any category and difficulty
Protonmail MCP Server
Send Protonmail emails via Claude and VSCode
Grok MCP Plugin
Seamless Grok AI integration for Cline